overleaf skabelonsgalleriLaTeX templates and examples — Recent
Opdag LaTeX skabeloner og eksempler til at hjælpe med alt fra at skrive en artikel til at bruge en specifik LaTeX pakke.

This template can be used for the submission to IMAV 2024 conference.

Thesis template for Nha Trang University.

一个西工大简历模板,请务必使用XeLaTeX编译。

PhD at Energy Transition in Politecnico Di Torino, Turin Italy
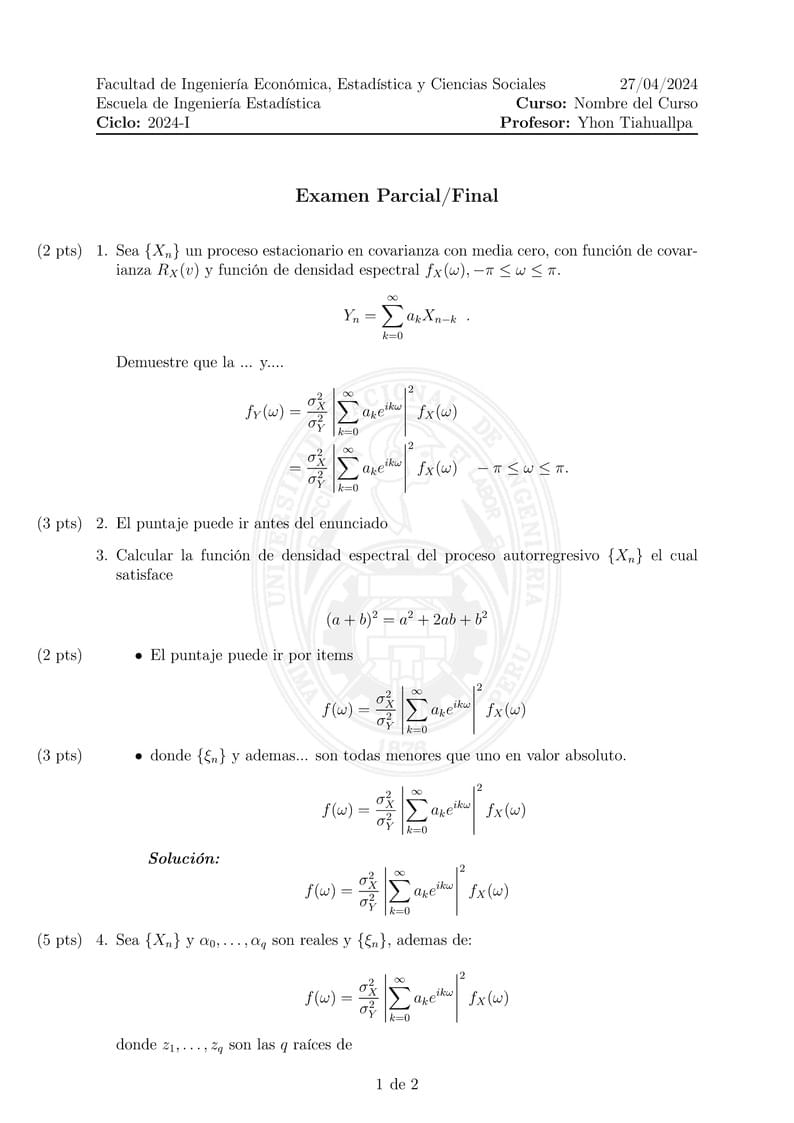
Esta plantilla está diseñada para la creación de exámenes de parciales o finales Cuenta con un diseño de fondo personalizado, cabeceras detalladas y pies de página con numeración automática. Incluye una sección de preguntas con espacios para los puntos asignados y está configurada para facilitar la escritura de ecuaciones complejas y fórmulas matemáticas. Además, ofrece la flexibilidad de añadir notas al margen y es adecuada para pruebas parciales o finales en la Facultad de Ingeniería Económica, Estadística y Ciencias Sociales, Universidad Nacional de Ingeniería. #UNI #FIEECS #EPIES #Examen #Parcial #Final #Universidad-Nacional-de-Ingeniería

PFE Report Template for INPT students.

Template for the Instituto Superior de Engenharia do Porto (ISEP), DEE, LEEC and LETI students to prepare Presentations.

A thesis template adapted from one bequeathed by Leanne Nortje. The proper distro is at https://ctan.org/pkg/stellenbosch-2, this one is for dummies, as I was when I was a student.

This is the unofficial TU Eindhoven beamer template, developed by Jens d'Hondt.
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.